The US Federal Bureau of Investigation stated in their annual Internet crime report that Internet fraud including impersonation and phishing contributed to $4.2 billion losses in 2020 [3]. This is critical for financial institutions because regulations often require them to refund the lost money to victimized customers.
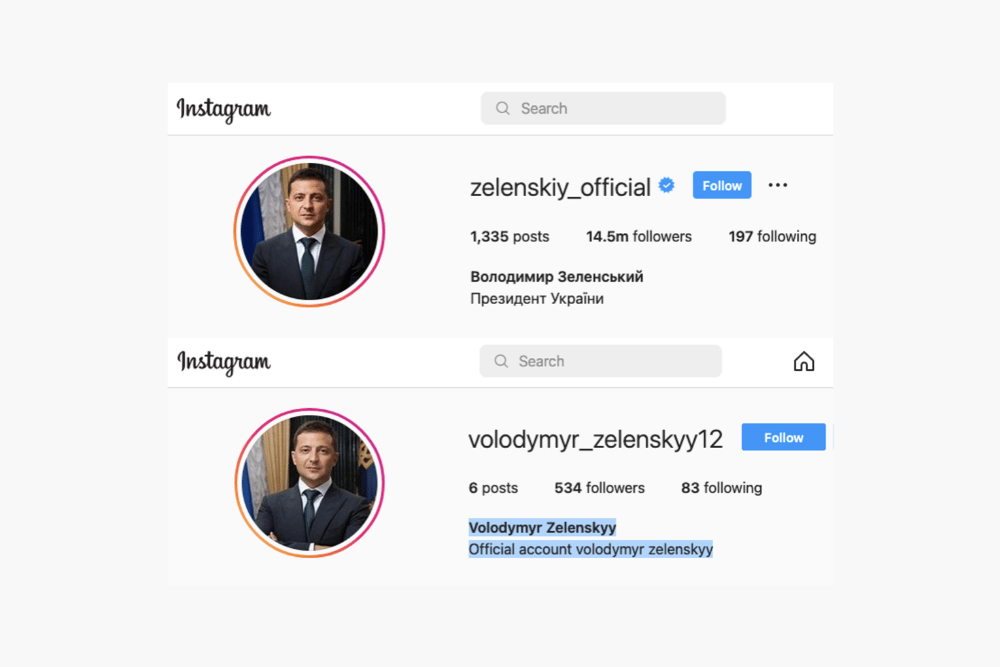
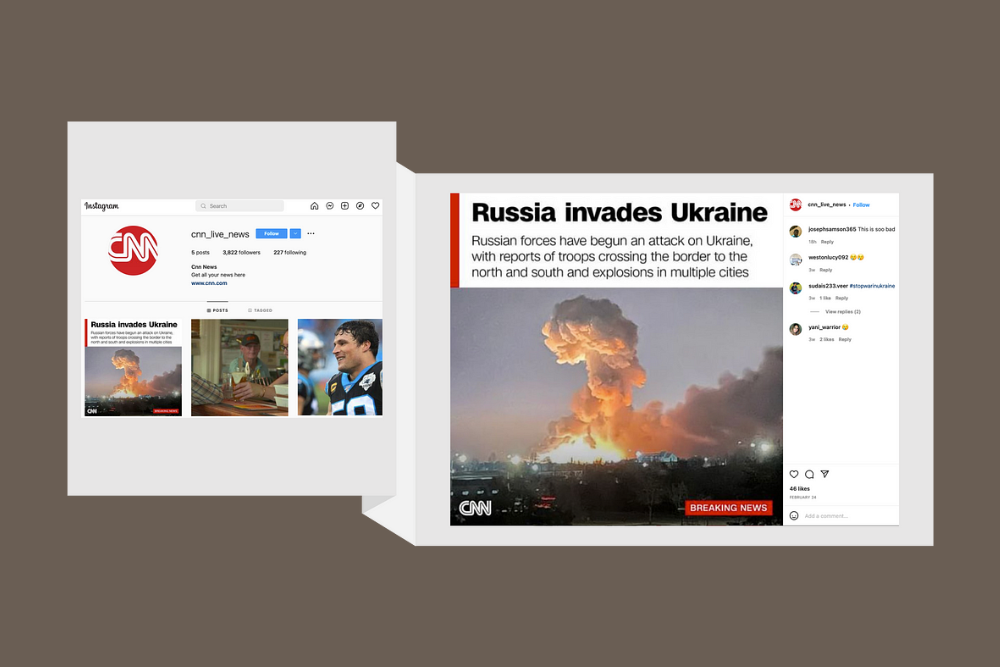
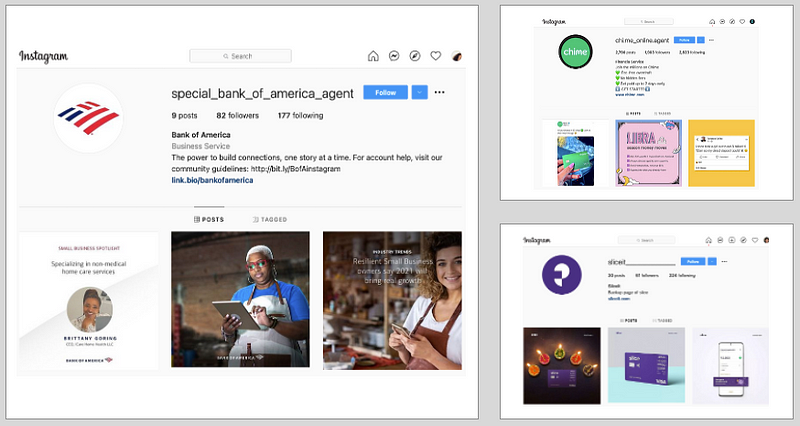 Figure 1: Brand phishing and impersonation accounts on Instagram
Figure 1: Brand phishing and impersonation accounts on Instagram
Email versus Social Media Phishing
Email has been the major phishing attack vector over the years. However, due to the rise of social media (Facebook, Instagram, LinkedIn), brand phishing attacks on social media platforms have increased exponentially over the last few years [2].
Social Media Phishing Examples
Let’s consider two examples of brand phishing on social media.
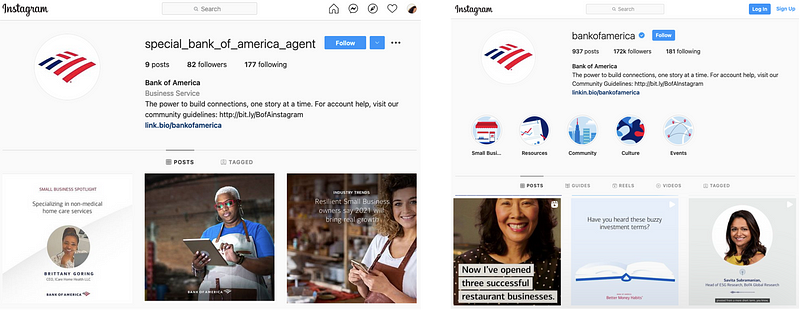
Bank of America is one of the largest financial institutions in the world, serving small, medium, and large corporations with investment and financial solutions. Figure 2 shows their Instagram account, which has more than 172K followers and 930 posts. Figure 2 also shows a phishing account that attempts to impersonate Bank of America.
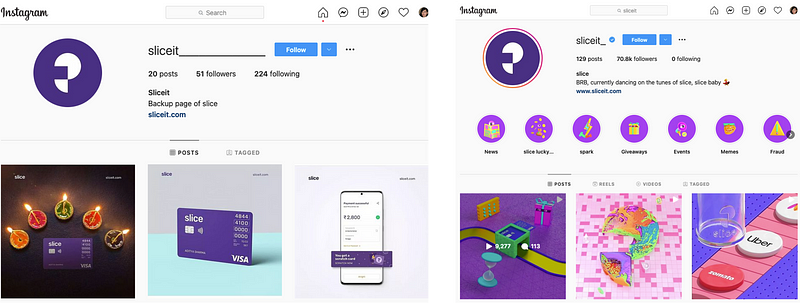
Slice is a fintech startup company based in India that offers its customers a simple financial platform to pay bills and manage expenses while receiving rewards for using their platform.
Even though it is a new company, Slice has not been exempt from phishing. Scammers have created fake Instagram accounts similar to the real Slice account that has over 70K followers. The visual similarity between the real and fake accounts can increase scammer’s effectiveness in defrauding Slice’s customers and stealing their financial information related to their Slice card.
Anatomy of a Phishing Attack on Social Media
Cyber-criminals can attack a business or a brand on social media using two approaches. First, they can create a new account that is similar to the brand’s real account. Second, they can hack into and take over an existing account, with a large number of followers, and make the hacked account look similar to the brand’s real account.
The examples in this article focus on brand phishing on Instagram. However, similar attacks happen on other social media platforms such as Facebook, Twitter, and LinkedIn.
Let’s take Chime as an example to explain the two types of brand phishing attacks. Chime is an American financial technology company that offers mobile banking services. Their official Instagram has more than 687K followers.
First Approach: Creating a New Account
The attacker often starts by creating a new impersonation account that looks very similar to the legitimate account page of the company being targeted. The company logo, images, posts, and text are copied over.

However, there are some aspects of the legitimate page that are harder to replicate e.g. the number of followers and the history of posts in the real account. To address the number of followers, the attacker can buy followers. One statistic puts the price tag at $12 for 1,000 followers on Instagram.
The impersonation account is often crafted carefully to mislead customers of the brand. For example, the account handle name looks similar to the brand’s name. It may contain words such as service, support, winner, etc. that makes it appear believable. In this example, the phishing account handle contains the words Chime and winner.
After setting up the impersonation account, the attacker is ready to send direct messages (DM) to the followers of the official Chime account asking them for personal and financial information related to Chime. The attacker can include links that redirect to external phishing websites that contain a fake account login page. The impersonation account in this example, sent messages stating that the follower had been selected as the winner for a giveaway conducted by Chime.
Second Approach: Account Takeover
To make the impersonation account look more legitimate, attackers can take over existing accounts on Instagram. These accounts can be Instagram verified accounts or accounts that have existed for a long time and have a large number of followers.
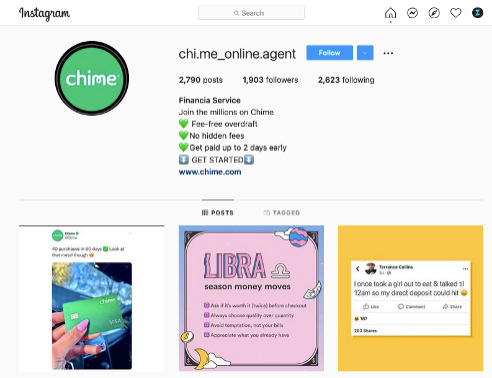
Figure 5 shows an example of an account taken over by an attacker. The account has more than 1,900 followers and 2,790 posts. After taking over the account, the attacker changed the profile information to resemble the targeted company’s name, logo, and images. The latest posts have been copied over from the official Chime account.
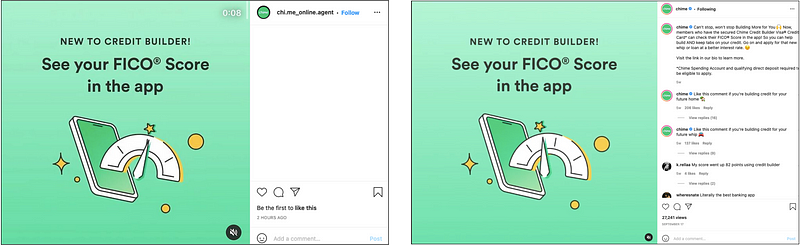
Figure 6 shows a post duplicated from the official account. Notice that the post in the official account has comments and likes from the followers of the official account. Another observation on the phishing account is that these new, copied-over posts have no relation to older posts by the actual owner of that account.

Figure 7 shows posts from the original owner before the account was taken over. The posts go back a few years with comments and likes from the account’s original followers.
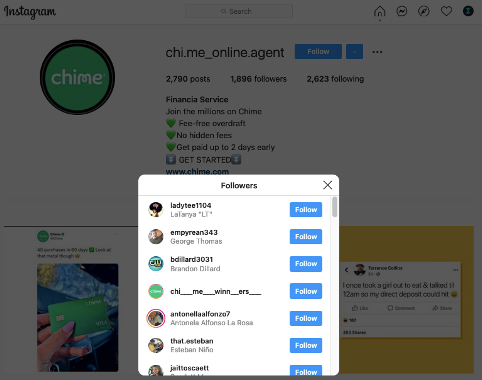
Figure 8 shows some of the followers of the hacked account. When sending phishing links and direct messages from this account, the attacker may fool users more easily because the account has a large number of followers, which can make the account appear more trustworthy to an unsuspecting user. The existing followers of the account may also be tricked and some of them may become victims. The threat of users falling for the phishing attempts will continue until Instagram takes down the account.
Social Media Phishing Protection
Many existing cybersecurity techniques that detect phishing attacks for websites are not effective in the social media context.
These techniques often focus on detecting phishing using URL analysis, checking domain name blacklists, and IP reputation analysis. However, these methods do not work for social media platforms like Instagram, Facebook, or LinkedIn because they are listed as safe domains and have good IP reputation.
We need new, more advanced techniques to protect brands and users from social media phishing. One way is using AI and deep learning models to do a visual analysis of accounts including their posts, images, logos, fonts, and color schemes.
At Eydle, we use artificial intelligence to protect brands from social media phishing. Eydle’s deep learning-powered platform can identify and take down impersonation accounts before they can harm a brand’s customers. Contact us at [email protected] to learn more.
References
[1] “2021 Data Breach Investigations Report | Verizon.” https://www.verizon.com/business/resources/reports/dbir/ (accessed Oct. 23, 2021).
[2] “Outseer TM Fraud & Payments Report Q3 2021,” OutseerTM. https://outseer.com/fraud-report-q3-2021/ (accessed Oct. 27, 2021).
[3] “IC3 Releases 2020 Internet Crime Report — FBI.” https://www.fbi.gov/news/pressrel/press-releases/fbi-releases-the-internet-crime-complaint-center-2020-internet-crime-report-including-covid-19-scam-statistics (accessed Oct. 23, 2021).